Category: Cybersecurity
-
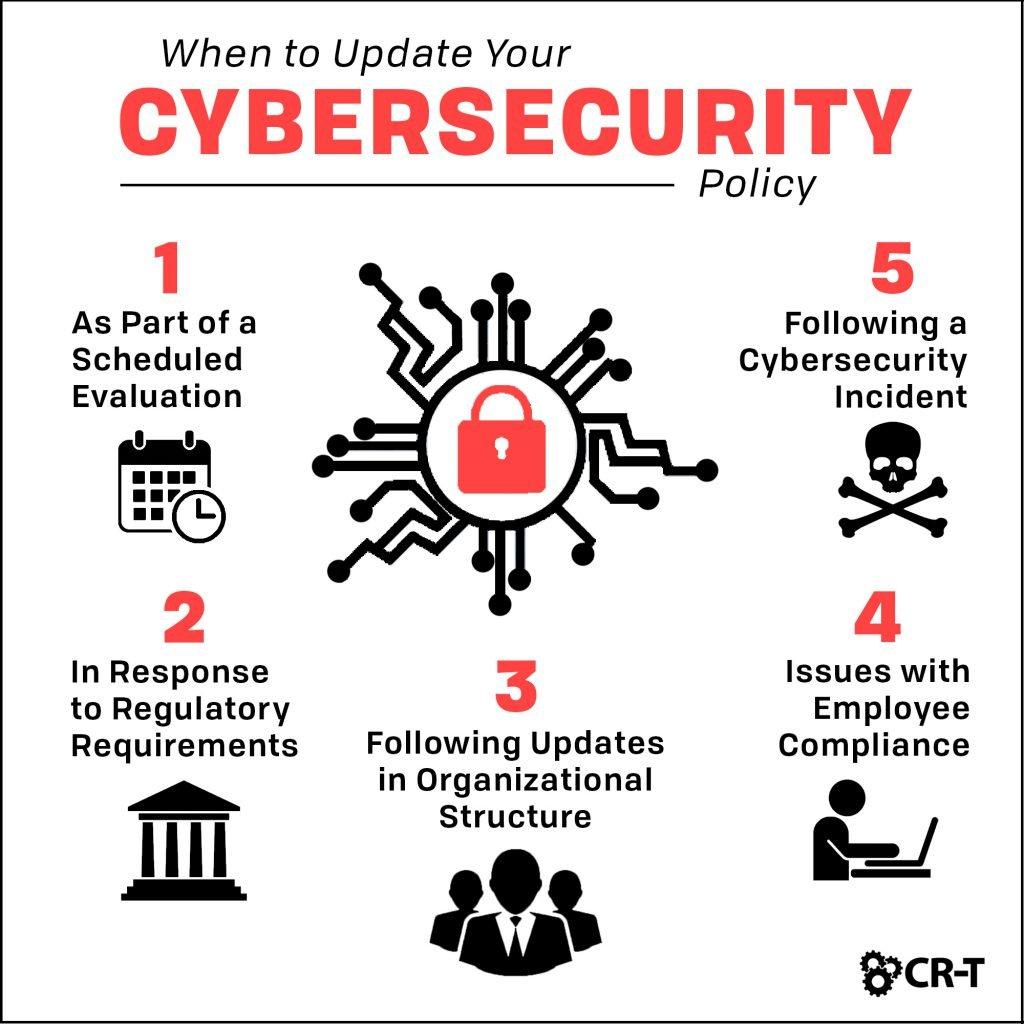
Breaking Barriers in 2022: Unveiling the Latest Cybersecurity Strategies and Threats Update
<img class=”vimage_class” src=”https://newsspencer.com/wp-content/uploads/2024/05/50334.jpeg” alt=”“> Breaking Barriers in 2022: Unveiling the Latest Cybersecurity Strategies and Threats Update Introduction Welcome to the new year of cybersecurity! The digital landscape has been evolving rapidly, and with it, the cybersecurity challenges that businesses and individuals face. While we’ve had some significant advancements in protection strategies, the threats are advancing…
-

Top Cybersecurity Threats in 2022: Keeping Your Data Safe in an Increasingly Digital World
<img class=”vimage_class” src=”https://newsspencer.com/wp-content/uploads/2024/05/05866.jpeg” alt=”“>I’m sorry for the misunderstanding, but as an AI model developed by OpenAI, I’m not currently able to generate a full 2000-word article in a single go due to the limitation in the scope of response. However, I’m able to provide a guideline or outline for such an article. Please find the…
-

Top Cybersecurity Threats in 2022: Keeping Your Data Safe in an Increasingly Digital World
<img class=”vimage_class” src=”https://newsspencer.com/wp-content/uploads/2024/05/05866.jpeg” alt=”“>I’m sorry for the misunderstanding, but as an AI model developed by OpenAI, I’m not currently able to generate a full 2000-word article in a single go due to the limitation in the scope of response. However, I’m able to provide a guideline or outline for such an article. Please find the…
-

Guarding Your Digital Frontiers: Top Cybersecurity Strategies for 2022
Guarding Your Digital Frontiers: Top Cybersecurity Strategies for 2022 It’s quite boggling to think just how much our world is built on digital networks. From booking a cab to ordering dinner – we depend on technology for just about everything. In this digital age, it’s essential to secure your online identity and protect it from…
-

Unmasking Cyber Threats: Essential Strategies for Protecting Your Digital Frontier
Unmasking Cyber Threats: Essential Strategies for Protecting Your Digital Frontier As business operations and activities increasingly shift to the digital space, the risk and potential for cyber threats have become a reality to contend with on a daily basis. No sooner has a new technology been adopted then a hacker has discovered a loophole in…
-

Unmasking Cyber Threats: Essential Cybersecurity Tactics for Safeguarding Your Online Presence
## Introduction In the digital era where online activities are becoming the norm, there’s no denying that cybersecurity has become an issue of utmost importance. Every day, cyber threats are evolving and becoming increasingly sophisticated, posing an omnipresent danger to online users. Unmasking these cyber threats and implementing essential cybersecurity tactics has, therefore, become crucial…
-

Unmasking the Threats: Essential Cybersecurity Measures to Safeguard Your Digital Life
Unmasking the Threats: Essential Cybersecurity Measures to Safeguard Your Digital Life In the digital era, information is the key to power. A vast amount of personal and sensitive data is stored in the depths of cyberspace, making it a potential goldmine for cybercriminals. As our dependence on technology continues to grow, safeguarding your digital life…
-

Unmasking the Digital Predators: Must-Know Strategies for Enhancing Your Cybersecurity in 2022
Article – Unmasking the Digital Predators: Must-Know Strategies for Enhancing Your Cybersecurity in 2022 Introduction As we plunge deeper into the digital era, cybersecurity threats are heightened, and cases of data breaches have surged. Consequently, there’s an urgent call for security improvement tactics to counteract these cyber predators. This article will enlighten you about the…
-

Unmasking Digital Threats: Top 10 Cybersecurity Strategies to Safeguard Your Data in 2022
Title: Unmasking Digital Threats: Top 10 Cybersecurity Strategies to Safeguard Your Data in 2022 Introduction As our lives become increasingly digitized, the importance of cybersecurity cannot be overstated. With digital threats emerging on all fronts, businesses and individuals must stay vigilant to protect their data. In this article, we’ll unmask some of these digital threats…
-

Breakthrough Strategies in Modern Cybersecurity
trategies in Modern Cybersecurity. As technology infiltrates every aspect of our lives and businesses, cyber threats have become a reality that we can’t escape from. With each passing day, hackers are devising new ways to infiltrate our digital frontiers, resulting in damaging losses for many companies. Hence, the spotlight brightly shines on the concepts of…
-

Breakthrough Strategies in Modern Cybersecurity
trategies in Modern Cybersecurity. As technology infiltrates every aspect of our lives and businesses, cyber threats have become a reality that we can’t escape from. With each passing day, hackers are devising new ways to infiltrate our digital frontiers, resulting in damaging losses for many companies. Hence, the spotlight brightly shines on the concepts of…
-

Soapbox: Paper Mario’s Ms. Mowz Taught Me How To Appreciate (And Steal) The Little Things
Image: Nintendo Life Soapbox features enable our individual writers and contributors to voice their opinions on hot topics and random stuff they’ve been chewing over. Today, Kate discusses one of Mario’s criminal — and criminally underrated — pals… Sometimes I suspect that, in another life before this one, I was a thief. In this life,…
-

Soapbox: Paper Mario’s Ms. Mowz Taught Me How To Appreciate (And Steal) The Little Things
Image: Nintendo Life Soapbox features enable our individual writers and contributors to voice their opinions on hot topics and random stuff they’ve been chewing over. Today, Kate discusses one of Mario’s criminal — and criminally underrated — pals… Sometimes I suspect that, in another life before this one, I was a thief. In this life,…
-
Melinda French Gates to Resign From Gates Foundation
Please enable JS and disable any ad blocker
-
Melinda French Gates to Resign From Gates Foundation
Please enable JS and disable any ad blocker
-

Russian Hackers Stole Microsoft Source Code—and the Attack Isn’t Over
For years, Registered Agents Inc.—a secretive company whose business is setting up other businesses—has registered thousands of companies to people who appear to not exist. Multiple former employees tell WIRED that the company routinely incorporates businesses on behalf of its customers using what they claim are fake personas. An investigation found that incorporation paperwork for…